Check for New/Modified Security Rules *
Cadence Weekly
Sites developmentproduction
| Initial | Recurring | |
|---|---|---|
| Estimated Time | 5 min | 5 min |
Benefits:
- Increase awareness
- Increase reaction times
Goal
Ensuring that security rules are tightly managed and governed is arguably the most important aspect of managing a Qlik site from an administrator’s perspective. This area is critical to ensuring the right people have access to the appropriate resources, and have the appropriate privileges to act on those resources. It is important to see if new rules are being created, and it is also very important to check rules that have recently been modified. This section will cover both.
Note
This page will outline two methods for accomplishing this activity (using the QMC and using a Qlik CLI for Windows script). The QMC approach is generally appropriate for most environments. The Qlik CLI for Windows approach is more appropriate for environments where automation is required.
Table of Contents
- QMC - Security Rules
- Get List of New/Modified Security Rules (Qlik CLI for Windows)
- Backup Security Rules
QMC - Security Rules
In the QMC, select Security Rules:
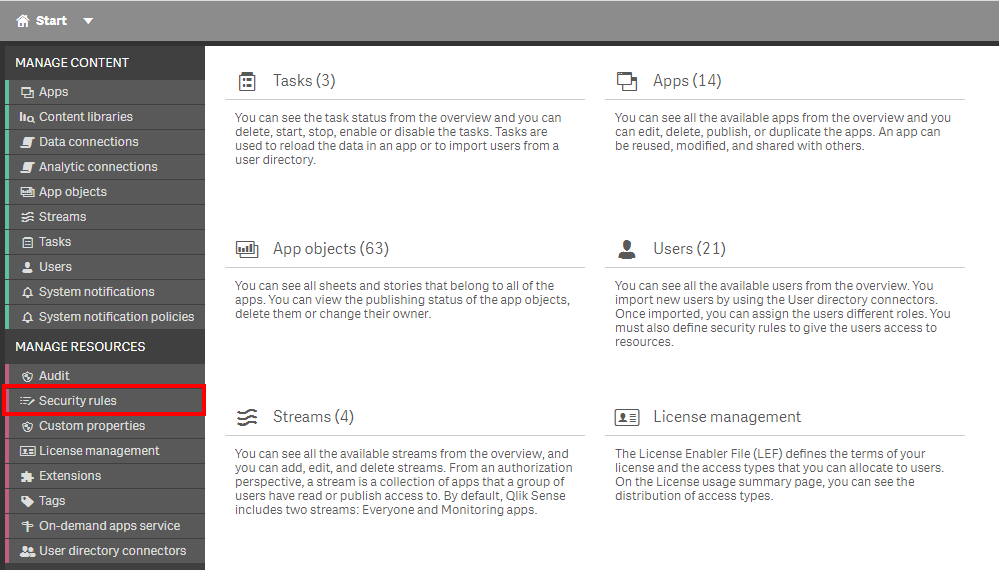
In the upper right hand side of the screen, select the Column selector, and then select the Created, Last Modified, and Modified by columns.
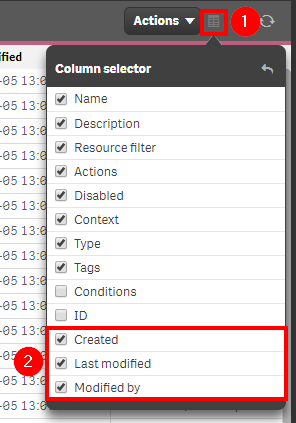
Now select the filter icon for the Created column, and then select the filter of Last seven days, or the desired range.
Lastly, review the resulting table and view any new security rules. Repeat this process for the Last modified column, reviewing what security rules were modified and by whom.
Get List of New/Modified Security Rules (Qlik CLI for Windows)
The below script snippet requires the Qlik CLI for Windows.
The script will bring back any security rules with a Created Date or Modified Date that is greater than or equal to x days old. The script will then store the output into a desired location in either csv or json format.
Script
# Function to collect security rules that were created or modified in the last x days
################
## Parameters ##
################
# Assumes default credentials are used for the Qlik CLI for Windows Connection
# machine name
$computerName = '<machine-name>'
# leave empty if windows auth is on default VP
$virtualProxyPrefix = '/default'
# set the number of days back for the app created date
$daysBack = 7
# directory for the output file
$filePath = 'C:\tmp\'
# desired filename of the output file
$fileName = 'new_security_rules'
# desired format of the output file (can be 'json' or 'csv')
$outputFormat = 'json'
################
##### Main #####
################
# create filePath
if (Test-Path $filePath) {
} else {
New-Item -ItemType directory -Path $filePath | Out-Null
}
# set the output file path
$outFile = ($filePath + $fileName + '_' + $(Get-Date -f "yyyy-MM-dd") + '.' + $outputFormat)
# set the date to the current time minus $daysback
$date = (Get-Date -date $(Get-Date).AddDays(-$daysBack) -UFormat '+%Y-%m-%dT%H:%M:%S.000Z').ToString()
# set the computer name for the Qlik connection call
$computerNameFull = ($computerName + $virtualProxyPrefix).ToString()
# connect to Qlik
Connect-Qlik -ComputerName $computerNameFull -UseDefaultCredentials -TrustAllCerts
# check the output format
# get all security rules that were modified or created >= $date
# output results to $outfile
If ($outputFormat.ToLower() -eq 'csv') {
Get-QlikRule -filter "(createdDate ge '$date' or modifiedDate ge '$date') and category eq 'Security'" -full | ConvertTo-Csv -NoTypeInformation | Set-Content $outFile
} Else {
Get-QlikRule -filter "(createdDate ge '$date' or modifiedDate ge '$date') and category eq 'Security'" -full | ConvertTo-Json | Set-Content $outFile
}
Backup Security Rules
Given the Qlik CLI for Windows script above, that script could actually be modified to pull security rules (by removing the filter) on a scheduled basis and store them out to separate files at a desired cadence, so that if an administrator wanted to “roll back” changes, they could. Refer to an example here: Qlik Support - Exporting and Importing Security Rules.
Tags
#weekly
#asset_management
#security_rules